GRC to CRG
May 17, 2024
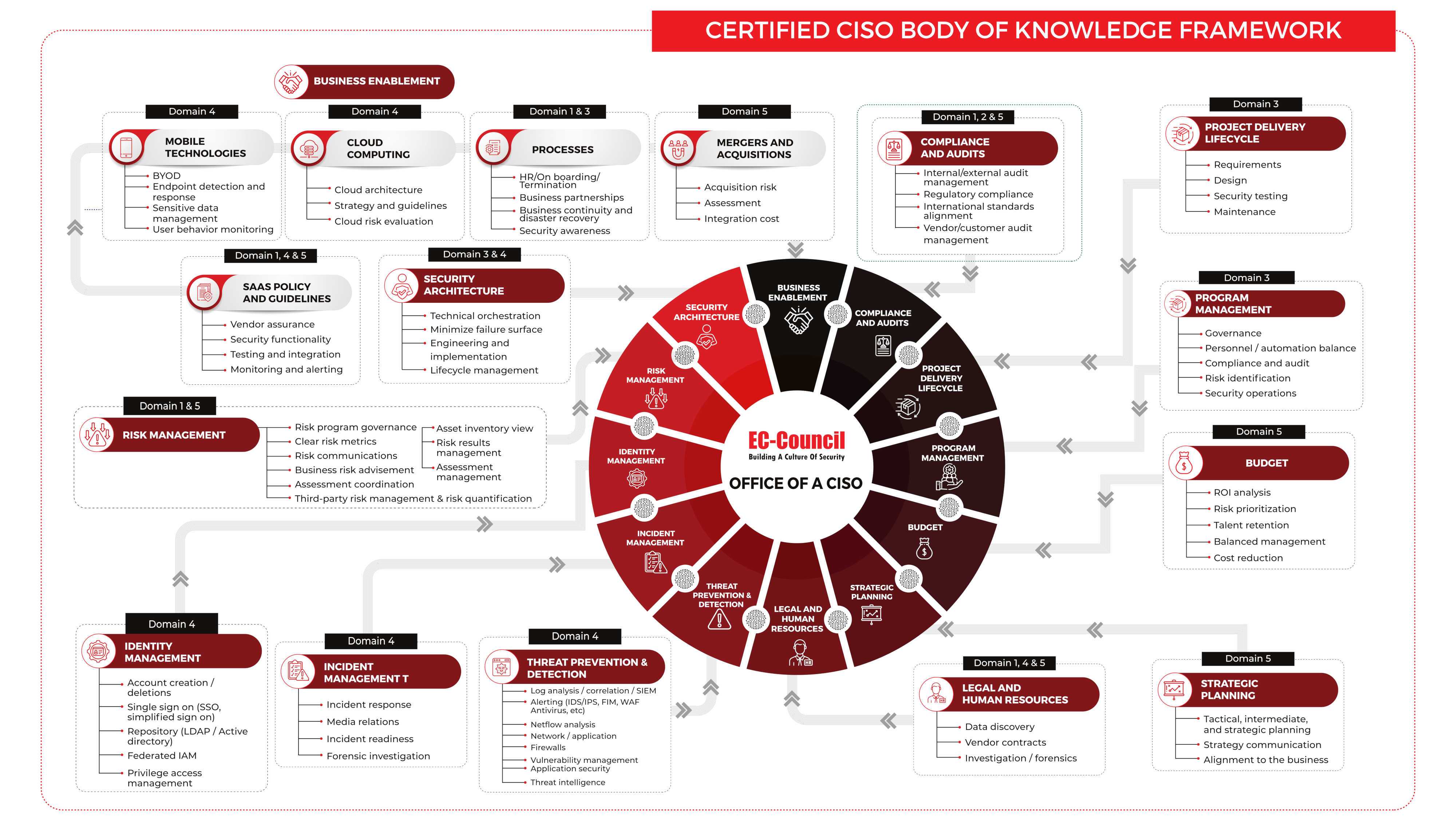
Photo Credit: ciso
Cyber Risk Governance (CRG) has emerged as one of the most significant challenges facing organizations in recent times. As cyber threats become more complex and frequent, enterprises are increasingly realizing the need for a comprehensive approach to managing these risks. In response, many companies have started adopting Governance, Risk Management (GRC) frameworks to address their cybersecurity concerns. However, traditional GRC approaches are limited in their ability to effectively manage cyber risk due to their focus on compliance and control management rather than the overall business impact of cyber threats. This has led many organizations to question the effectiveness of these approaches and search for better alternatives. The answer lies in Cyber Risk Governance (CRG). CRG is an integrated approach that combines strategic risk management with technical controls to enable organizations to proactively manage their cyber risks. Unlike traditional GRC approaches, which focus on identifying and mitigating risks after they occur, CRG emphasizes risk prevention through a combination of risk assessment, threat modeling, and risk mitigation strategies. CRG involves three key components:
- Strategic Risk Management - This component involves developing an enterprise-wide view of cyber threats and their potential impact on the business. This is achieved by conducting a comprehensive risk assessment that includes both IT and non-IT risks. The output of this process is a prioritized list of risk mitigation strategies.
- Technical Controls - This component involves implementing technical controls to prevent or minimize the impact of cyber threats. This can include measures such as data encryption, access controls, and network segmentation. The output of this process is a comprehensive set of technical controls that are designed to mitigate identified risks.
- Risk Mitigation - Finally, CRG involves actively managing cyber risk through ongoing monitoring and measurement of key performance indicators (KPIs). This component involves ensuring that technical controls are operating as intended and that the risk assessment process is continually updated to reflect changing business and technology environments. By adopting a CRG approach, organizations can turn GRC around to effectively manage their cybersecurity risks. By combining strategic risk management with technical controls, organizations can proactively address emerging threats before they become major incidents.
links: https://www.eccouncil.org/train-certify/associate-cciso/